Review a copy of your credit report at least once each year. Examples of how stolen personal information can be used to.
Compare receipts with account statements.

. Get 247 Live Member Support and Protect Your Identity. Ad Best Identity Theft Protection Services 2022. With the growth of technology protecting your personal information has never been more important.
Mining of Intrusion Detection Systems. Seeking Victims in Identity Theft Investigation. Proof of your address mortgage statement rental agreement or utilities bill Any other proof you have of the theftbills Internal Revenue.
This paper presents an evaluation of the. ConsumerVoice Provides Best Most Updated Reviews to Help You Make an Informed Decision. Online ID theft techniques investigation and response 77.
Watch for unauthorized transactions. A government-issued ID with a photo. Online organisations commonly use electronic commerce approaches.
Review your credit card and bank account statements. Fraudsters use a variety of techniques to acquire a victims card number. Tell us what happened.
IdentityTheftgov can help you report and recover from identity theft. And 3 social engineering. Online ID theft techniques investigation and response 77.
Ad Get Trusted Identity Theft Protection and Prevent Yourself From Becoming a Victim. 2 Identity theft has swiftly become a serious issue for victims police and prosecutors and is a. Ad Identity Theft happens to 1 Out of 4.
Compare Identity Theft Protection Reviews. Ad Answer Simple Questions to Make An ID Theft Affidavit On Any Device In Minutes. As technology advances so do the techniques used by identity thieves.
Compare Choose Your ID Protection Plan Today. Tell us as much as you can. HERES HOW IT WORKS.
Download Print Anytime. These techniques are listed under three headings. Get Protection from Identity Theft.
Shred receipts credit offers. Dont Be That One. Heres what you can do to spot identity theft.
Easily Customize Your ID Theft Affidavit. Join a Plan Today Starting 999. If you stop getting a bill that could be a.
For example training in identity theft usually involves providing investigators with the. Shred any documents with personal or financial information on them. However these have some limitations in the m-commerce.
Enroll in Minutes Now. Track what bills you owe and when theyre due. Notify the credit bureau in writing of any questionable entries.
The threat of identity theft is on the rise. Ad Our Technology Alerts You to a Wide Range of Identity Threats. The University of Glamorgan and is currently working towards a PhD in Data.
All Major Categories Covered. Identity Thieves are Smart. First file the theft with the Federal Trade Commission FTC and receive an identity theft affidavit which you will then take when you file the crime with the local police and get a police report.
See our ID Protection Reviews Find Who Is Rated 1. What you can do to detect identity theft. The ID Theft investigation framework disti nguishes the examination in the victims and the.
The process of investigating cybercrimes includes. The FBI is seeking victims whose personally identifiable information PII may have been misused between September 2018 and. Well ask some questions about your situation.
Taking a citizen complaint Locating the IP address of the suspect Gaining access to the IP address of the Internet service provider.

Identity Theft Investigations Insight Investigations

Pdf Online Id Theft Techniques Investigation And Response

Tips And Advice To Prevent Identity Theft Happening To You Europol
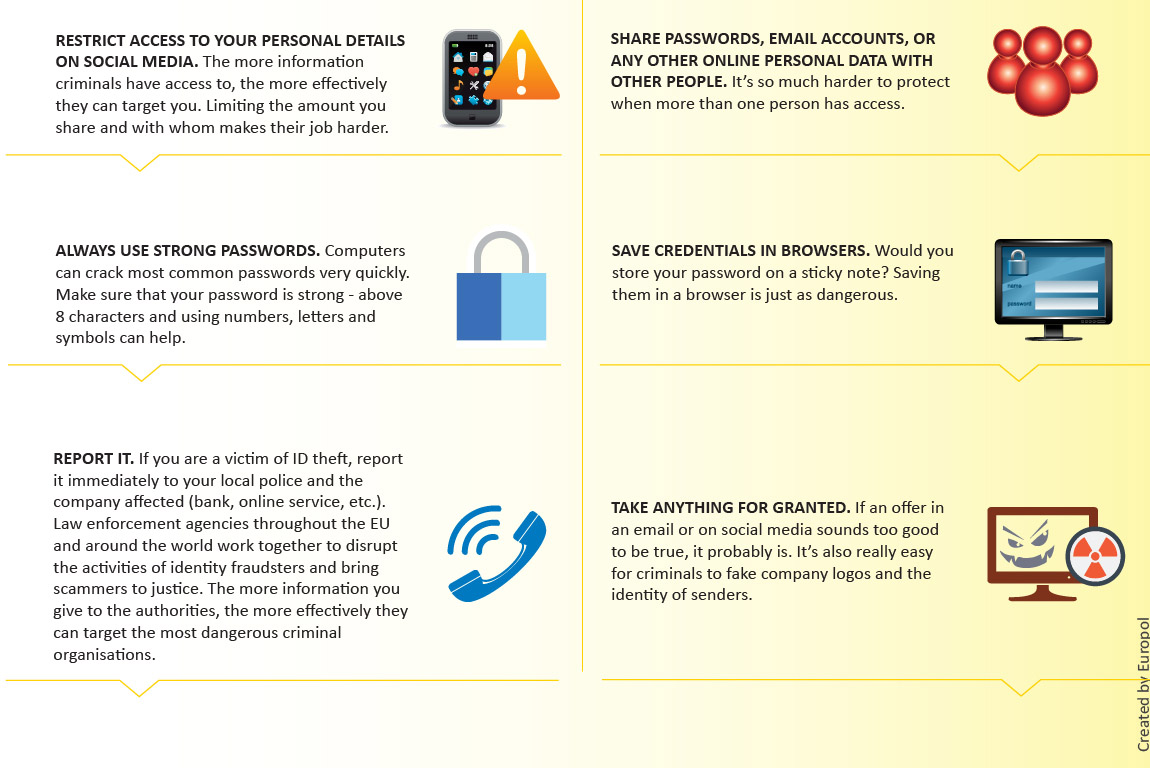
Tips And Advice To Prevent Identity Theft Happening To You Europol

Pdf Identity Theft Identity Fraud And Or Identity Related Crime



0 comments
Post a Comment